IT-Security in modern aviation

Aviation security extends far beyond the physical act of flying. Recent years have shown, that airlines and other actors in the aviation sector became increasingly interesting to groups with malicious intentions – e.g Hacker or Terrorists. Airports and airlines represent high-value targets for cyberattacks or incidents by third party.
This paper goes over points of interest in aviation, different approaches to interfere with aircrafts or infrastructure and the reaction of the ICAO and EUROCONTROL.
Table of Contents
Introduction
Regarding It-Security in the aviation sector, it is helpful to divide the field into three main areas, each with its own specific physical and technical security requirements.
At first General Aviation (GA) which considered for anything not commercially related to aviation. This includes small aircraft (e.g Cessna 172). This sector is mostly open to everyone and has the least security measures. Obviously, when heading to a large airport like Frankfurt, Munich, etc. there are more layers of security but when operating on local airfields you won’t face the same security layers.
Second, is commercial aviation, which has the greatest impact on all of us. Just in the USA, there are approximately 44.000 flights/day. This marks about 40% of all flights per day. Given the scale and the large number of passengers transported daily, it is crucial to implement robust security measures. These measures aim to address potential errors, such as human error or to prevent incidents
Third, is military aviation. Since this sector is highly classified – publicly known countermeasure would be dangerous for the individual military – there is not much information about Cybersecurity and security aspects in general.
Points of interest
With these sectors in aviation, we now identify potential points of interest for malicious actors as possible points of failure within each domain. This regards the following list
- Communication (Between Pilot and ATC)
- Passenger booking system
- Aircraft as an IT-system
Cyber threats on the ground
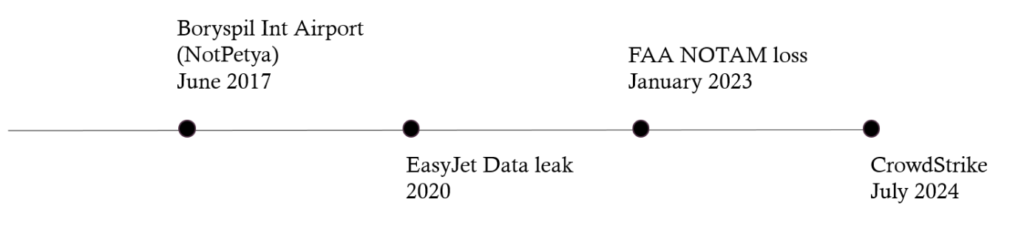
Aviation involves far more than simply transporting people or goods from one point to another. Before a plane can even take off, numerous background processes must take place. Each of them contributing either to flight safety or to the efficient and economic execution of operations. As previously mentioned, airports alone offer a wide range of potential targets. This not only applies to airports. Back in 2020 more than 60% off all attacks where targeting airlines with the goal to steal customer data or shutdown operational systems what caused airlines to stop operating temporary.
Obviously airlines are not the only potential targets but probably the most interesting ones
In flight vulnerabilities
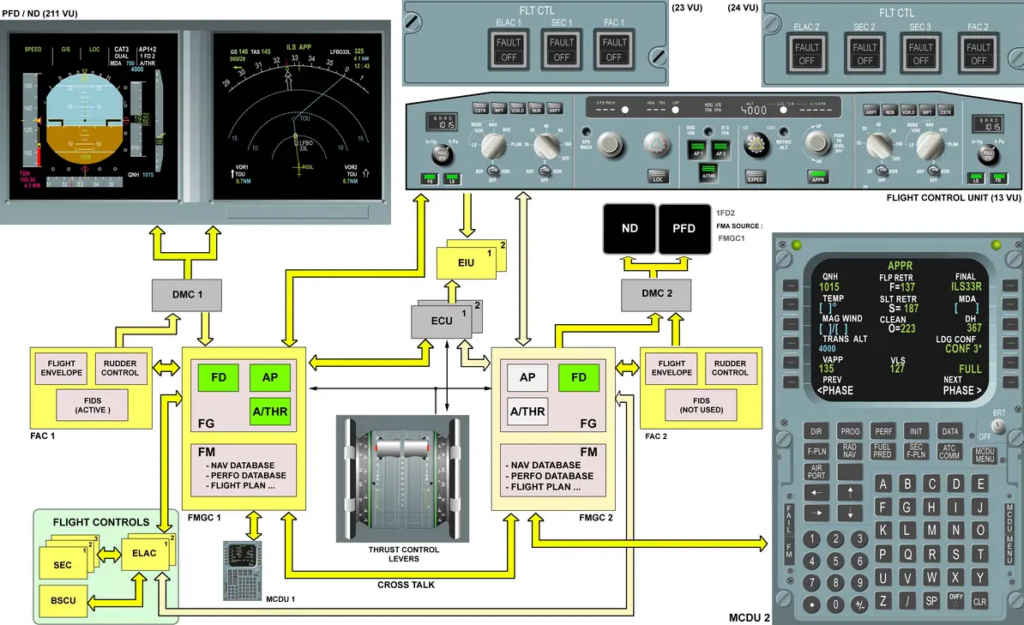
Let us take a modern aircraft such as the Airbus A320 as an example. Airbus equips its aircraft with a system known as „Fly by wire“. This technology enables a complete decoupling of the cockpit controls from the physical control surfaces of the aircraft. In other words, the pilot’s inputs are not transmitted mechanically but are instead processed and relayed electronically.
Before any input from the pilot is actually executed by the aircraft, it is first analyzed by multiple onboard computers. These computers determine whether the command falls within the aircraft’s operational limits. For instance, if the pilot pulls back on the side-stick to raise the aircrafts nose, the system checks parameters such as the current G-load and the angle of attack. If executing the input would result in exceeding these limits the system will intervene and prevent the command from being fully carried out.
In recent years, it has become increasingly clear that threats to aviation can arise even when the attacker is not in the immediate vicinity of the aircraft. From missile strikes in conflict zones to signal jamming and data manipulation within the cockpit, there is now a broad range of methods that pose serious risks to commercial aviation.
One threat that is currently gaining global significance is GPS-Jamming and Spoofing. Both techniques can produce similar effects in the cockpit by interfering with satellite-based navigation. The first option is to completely overwrite In both cases the result will be wrong data shown the pilots, starting with wrong positioning data, not accurate working clocks or even wrong indications of the GPW-system (Ground proximity warning system).
Results
The aviation industry became aware of digital threats relatively early. However, for many years, there were no unified regulations or cybersecurity standards across the sector. As a result, airlines often developed their own internal policies and practice to address emerging risks. For example in 2015 United Airlines launched a „Bug and Bounty“ program aimed to improve the security of their systems
One important step toward standardization was taken by the ICAO (International Civil Aviation Organization), which published the Cybersecurity Action plan back in 2020. This plan outlines a set of guidelines and recommended practices for airports, airlines and aviation related staff in general.
This plan lays the foundation for international cooperation across the aviation industry. It establishes common rules for incident management, emergency planning and the training of aviation personal in cybersecurity best practice.
In total the plan outlines 51 implementations, aimed at strengthening global cyber resilience in aviation